ANONYMIZE
SENSITIVE DATA.
PRESERVE ANALYTIC POWER.
WHAT YOU NEED
TO KNOW ABOUT ANONYMIZATION
What It Is
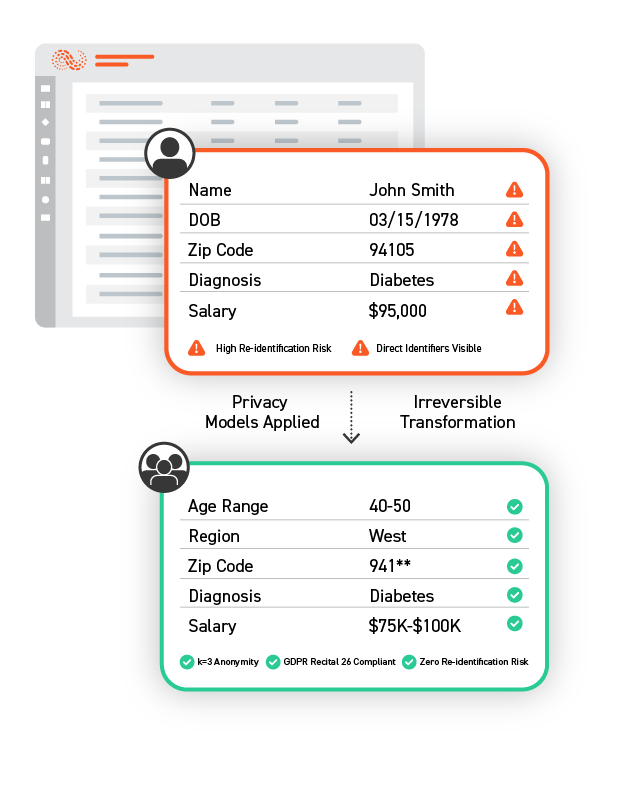
Anonymization permanently removes or generalizes identifiers so individuals cannot be re-identified. Protegrity models use industry-proven patterns and techniques to reduce residual risk while maintaining data utility.
When to Use It
Ideal for preparing sensitive data for AI or ML model training, analytics, or secure data sharing, and when regulatory requirements demand irreversible protection — particularly in healthcare, finance, and other highly regulated industries where personal identifiers must never resurface.
Why It Matters
Anonymization unlocks the full analytics value of sensitive datasets — without compromising compliance with industry mandates for PII, PCI, and PHI or regional requirements like GDPR Recital 26, HIPAA Safe Harbor, and CCPA. Teams can harness this valuable data to accelerate AI development, generate insights, and collaborate with partners while safeguarding personal information.
Why Our Anonymization IS Different
How Anonymization works
When Should You Use Anonymization?
Why Use Anonymization?
Anonymization delivers permanent privacy protection that satisfies the strictest regulatory requirements while preserving the full analytical value of your data.
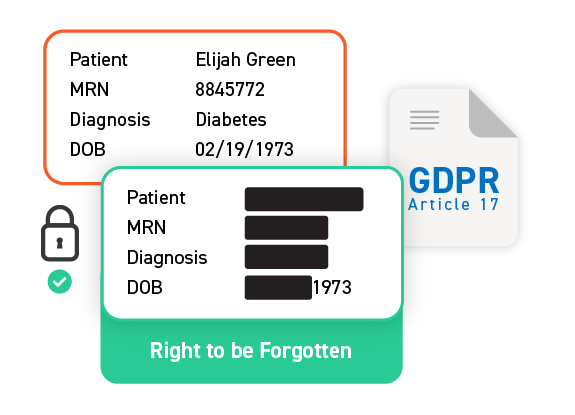
Irreversible Protection
Ensures compliance with “right to be forgotten” requirements.

Privacy-Preserving Analytics
Safely train AI models or run BI reports without exposing identities.

Data Mobility
Share anonymized datasets with external partners
or third parties confidently.

Long-term Retention
& Minimization
Keep data useful for historical trend analysis while
minimizing your compliance footprint.

Reduce Breach Liability
Anonymized datasets are outside breach notification scope –
reducing financial and reputational risk.
Beyond Anonymization: Comprehensive AI Protection
Text To Analytics
Semantic Guardrails
Synthetic Data Generation
Find & Protect
Explore Data-Centric
Data Protection
Discovery
Identify sensitive data (PII, PHI, PCI, IP) across structured and unstructured sources using ML and rule-based classification.
Learn MoreGovernance
Define and manage access and protection policies based on role, region, or data type—centrally enforced and audited across systems.
Learn MoreProtection
Apply field-level protection methods—like tokenization, encryption, or masking—through enforcement points such as native integrations, proxies, or SDKs.
Learn MorePrivacy
Support analytics and AI by removing or transforming identifiers using anonymization, pseudonymization, or synthetic data generation—balancing privacy with utility.
Learn MoreTake the
next step
See how Protegrity’s fine grain data protection solutions can enable your data security, compliance, sharing, and analytics.
Get an online or custom live demo.