Architect Secure Data Sharing at Scale
Data architects face the challenge of enabling seamless, secure data sharing across borders and complex ecosystems while protecting sensitive information like PII, PHI, and PCI. The stakes are high: with over 83% of organizations struggling to securely share data across borders, and sovereignty laws impacting 60% of enterprises, the need for innovation has never been greater.
Protegrity addresses these challenges with vaultless tokenization and centralized governance, ensuring data remains secure at its core. By unlocking the $1.5 trillion potential of cross-border data flows, our solutions empower organizations to share information securely across regions, enabling faster decision-making, driving innovation, and scaling operations while maintaining control and compliance.
83%
Organizations struggle with cross-border data sharing
60%
Sovereignty laws hinder global data sharing
$1.5T
Value of global cross-border data flows
50%
Faster decisions via secure data sharing
From Access Control to Tokenization: Secure and Seamless Data Sharing
Secure Collaboration Across Teams
Security architects must ensure sensitive data is safeguarded while enabling collaboration across hybrid and multi-cloud environments. The challenge is finding a solution that protects PII, PHI, and PCI data without creating roadblocks or exposing vulnerabilities. Protegrity provides the tools to secure data sharing with end-to-end protection. From encryption to tokenization, our platform ensures sensitive data flows securely between systems, teams, and regions—reducing risk while maintaining compliance and operational efficiency.
Design Systems for Safe, Scalable Data Sharing
Data architects face the growing demand for data sharing that fuels analytics and innovation. But balancing accessibility with security and compliance is no small task in complex, hybrid ecosystems. Protegrity helps data architects build scalable architectures with security at the core. Our centralized governance and vaultless tokenization make it possible to share sensitive data freely and safely, allowing architects to deliver systems that power collaboration without compromise.
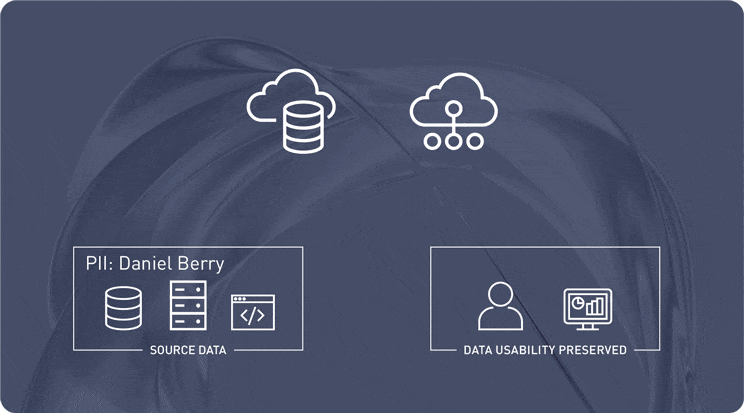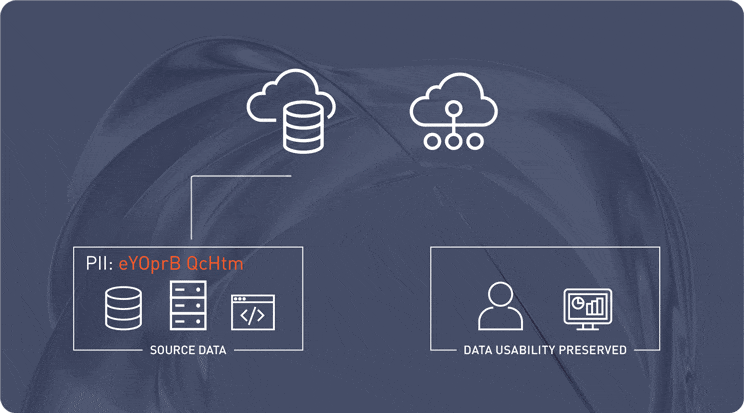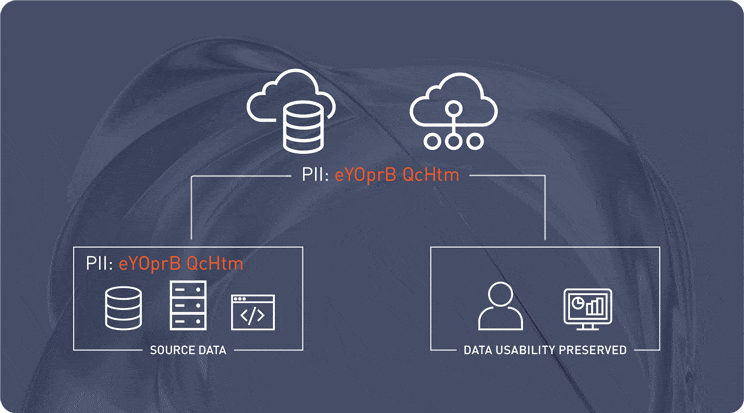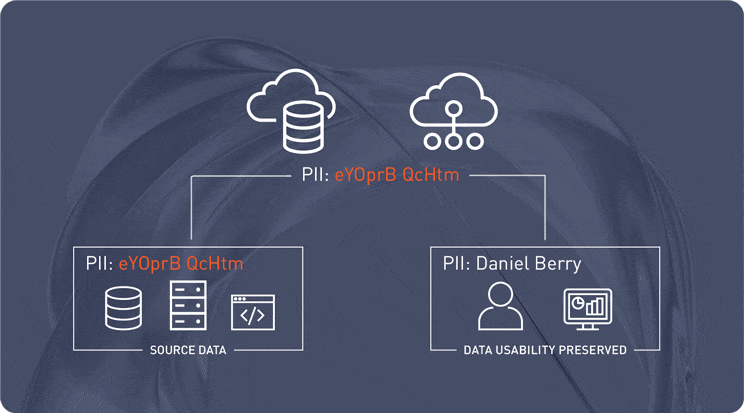
Protect Data with De-Identified Values and Vaultless Tokenization
Protegrity’s vaultless tokenization replaces sensitive data with anonymized values at the source, ensuring security from the start. This data-centric approach enables architects to secure information across hybrid and multi-cloud environments while preserving data usability for analytics and AI workflows.
Enable Secure Collaboration with Enterprise Security APIs
Protegrity integrates seamlessly with applications and systems through API-driven architecture, enabling secure and policy-enforced data sharing. Granular access controls and centralized policies ensure sensitive data flows securely across teams, regions, and platforms without vulnerabilities.
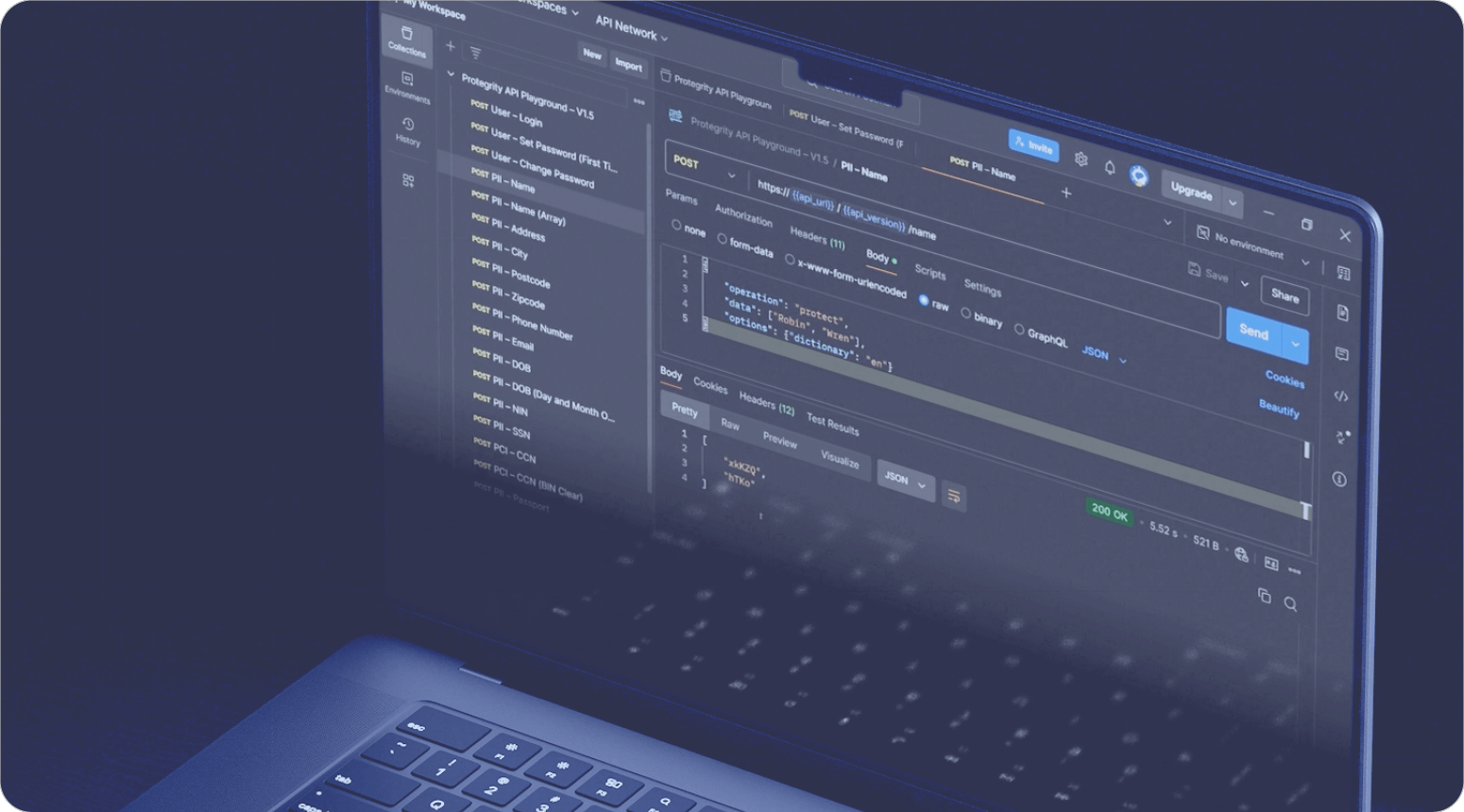
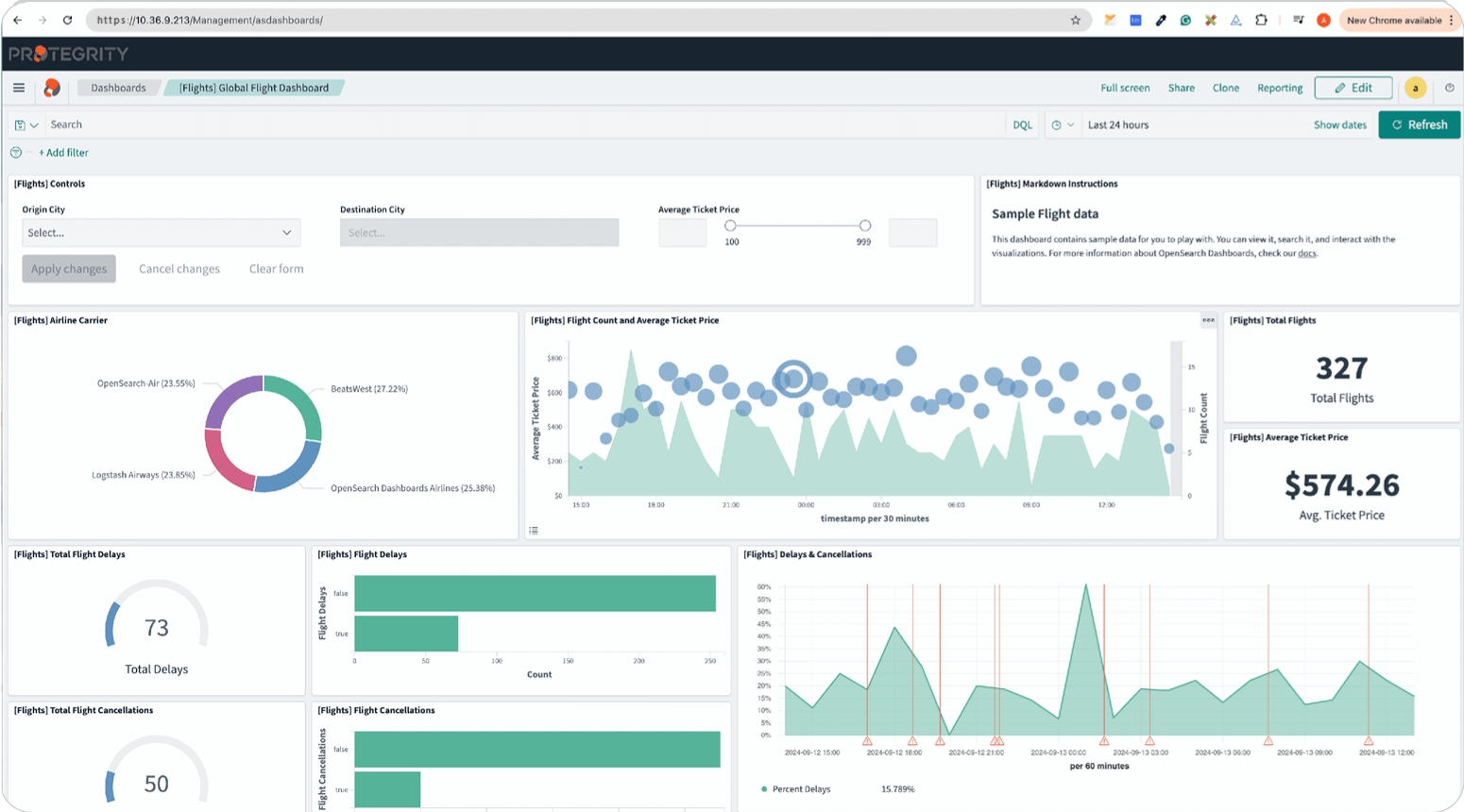
Monitor and Optimize Data Flows in Real-Time
Protegrity provides a centralized dashboard for real-time monitoring of data access and sharing activities. Security and data architects can visualize data flows, detect anomalies, and ensure compliance — all while optimizing performance for secure, efficient collaboration. Visual Suggestion: A live monitoring dashboard with data flows and access metrics.
Online Demo
Secure data sharing meets regulatory compliance.
Envision your organization’s future with an online or custom demo.
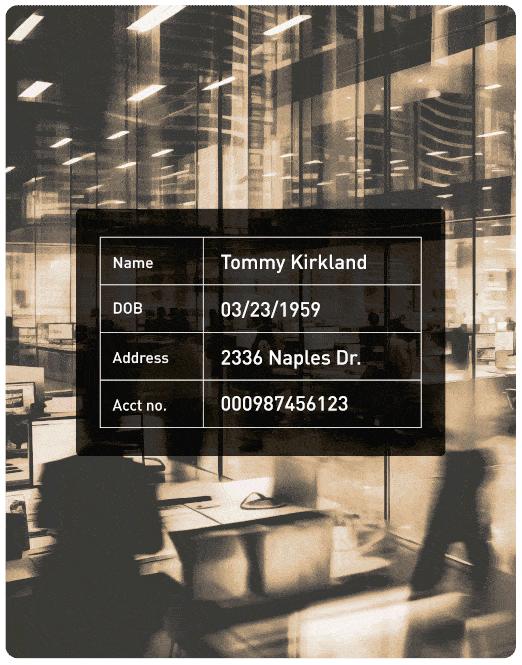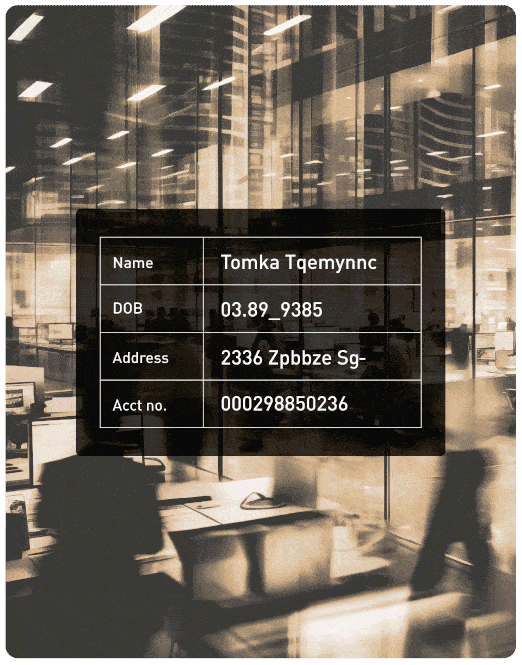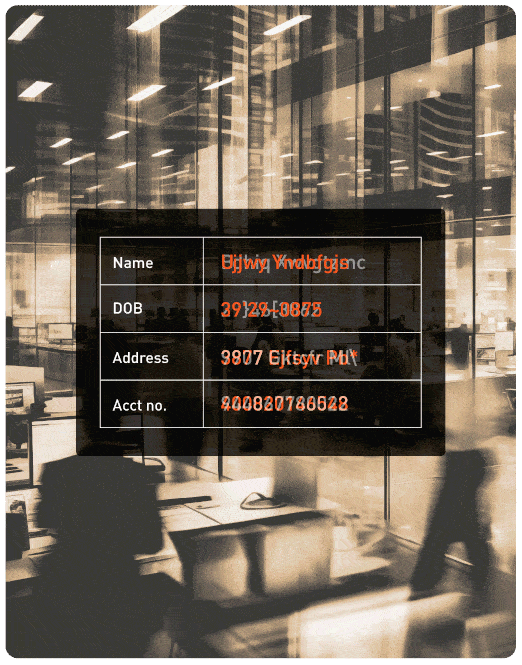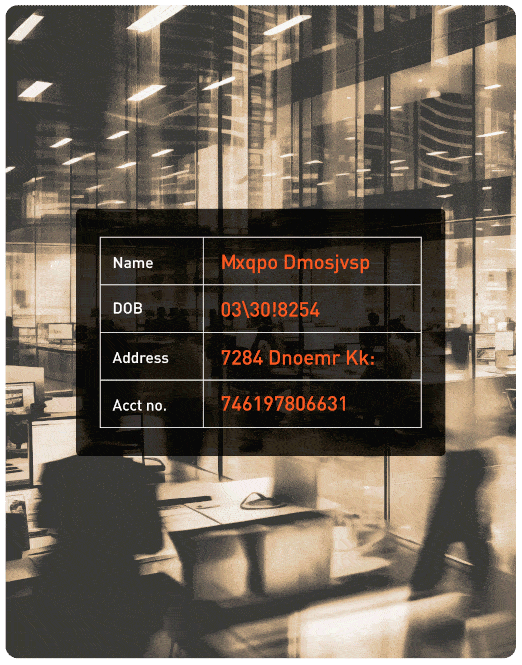

A global financial institution needed to securely migrate sensitive customer data to the cloud while maintaining scalability for analytics and AI. Protegrity enabled seamless data sharing across hybrid environments by applying vaultless tokenization and Enterprise Security APIs. The result? Reduced migration timelines by 30% and accelerated time-to-insight for global teams.
THE PROTEGRITY ADVANTAGE FOR DATA SHARING
Without Protegrity
- Fragmented and inconsistent data sharing: Sharing data across multiple systems and environments is unreliable, with conflicting governance requirements exposing sensitive data to compliance risks and operational bottlenecks, disrupting collaboration.
- Delays in sharing insights: Traditional methods create bottlenecks, limiting organizations’ ability to analyze and act on data in real-time, slowing innovation and decision-making.
- Limited usability due to rigid security: Standard security approaches force trade-offs between data protection and usability, limiting the ability to securely share data for analytics and collaboration.
- Increased exposure to breaches: Legacy access controls and siloed systems leave sensitive shared data vulnerable to interception during data exchanges, amplifying risk.
- Vendor lock-in and high costs: Inflexible tools limit integration with modern cloud ecosystems, driving up costs and complicating efforts to achieve seamless data sharing.
With Protegrity
- Seamless, scalable data sharing: Protegrity ensures consistent, secure sharing of sensitive data across platforms, environments, and hybrid systems, meeting governance and compliance requirements effortlessly.
- Accelerated collaboration and insights: Protegrity’s rapid data de-identification and tokenization enable faster analytics and insights, unlocking innovation and reducing time-to-value.
- Customizable data sharing solutions: Protegrity provides tailored protection, allowing safe, compliant sharing of sensitive data without compromising scalability or usability.
- Zero-trust protection for shared data: Protegrity enforces zero-trust principles, uniquely securing data at every level and ensuring no vulnerabilities are exposed during sharing.
- Optimized integrations for seamless sharing: Protegrity connects with AWS, Azure, GCP, and hybrid environments, enabling cost-effective, scalable, and secure data sharing with unmatched flexibility.
Seamless Data Sharing Architecture: Secure Collaboration with Built-In Protection
This architecture showcases how Protegrity enables secure and compliant data sharing across global and regional environments. By integrating centralized policy management with region-specific enforcement and secure data flows through protectors and APIs, organizations can ensure seamless collaboration while safeguarding sensitive information. Each step demonstrates how Protegrity’s solution addresses the challenges of maintaining security and compliance in complex, multi-cloud ecosystems.
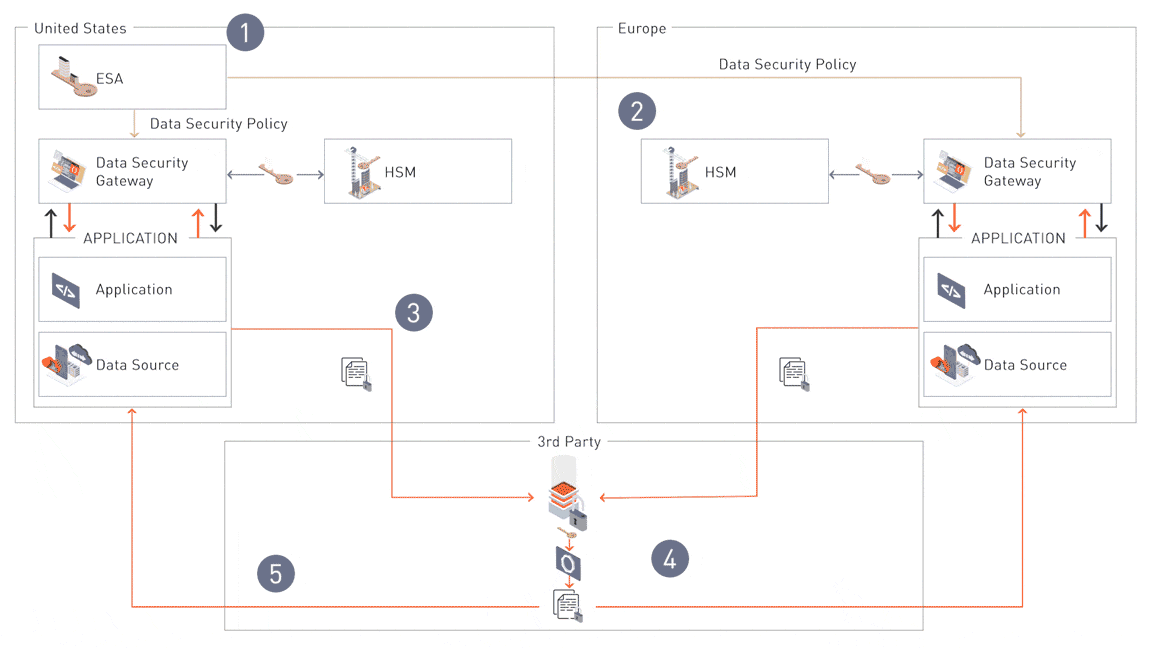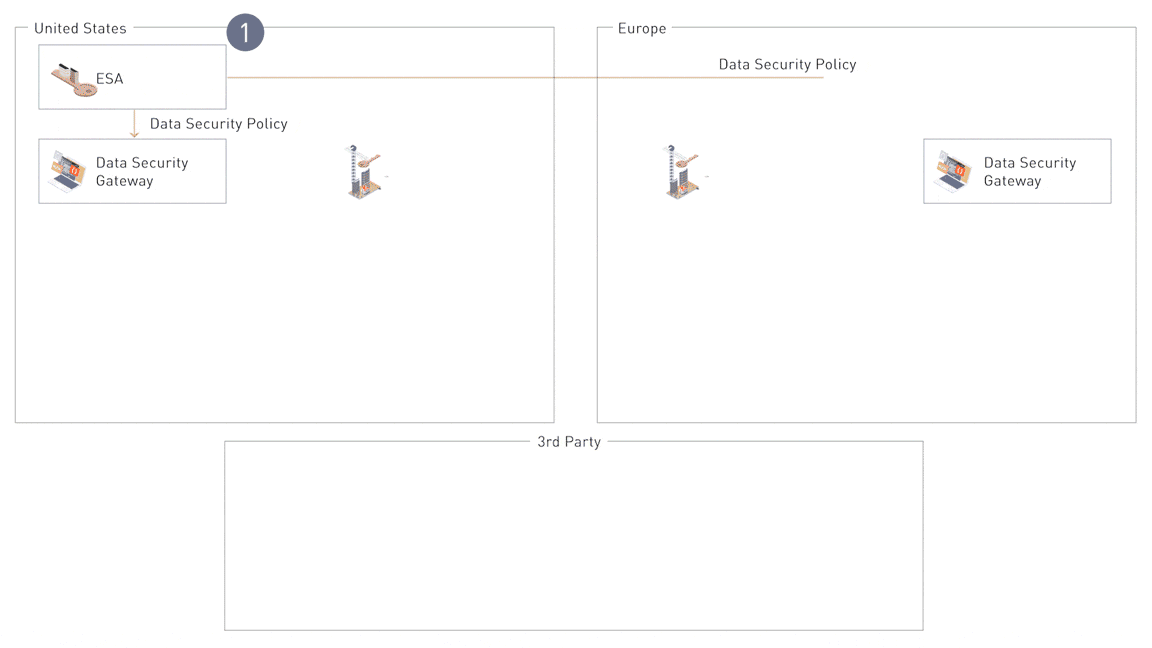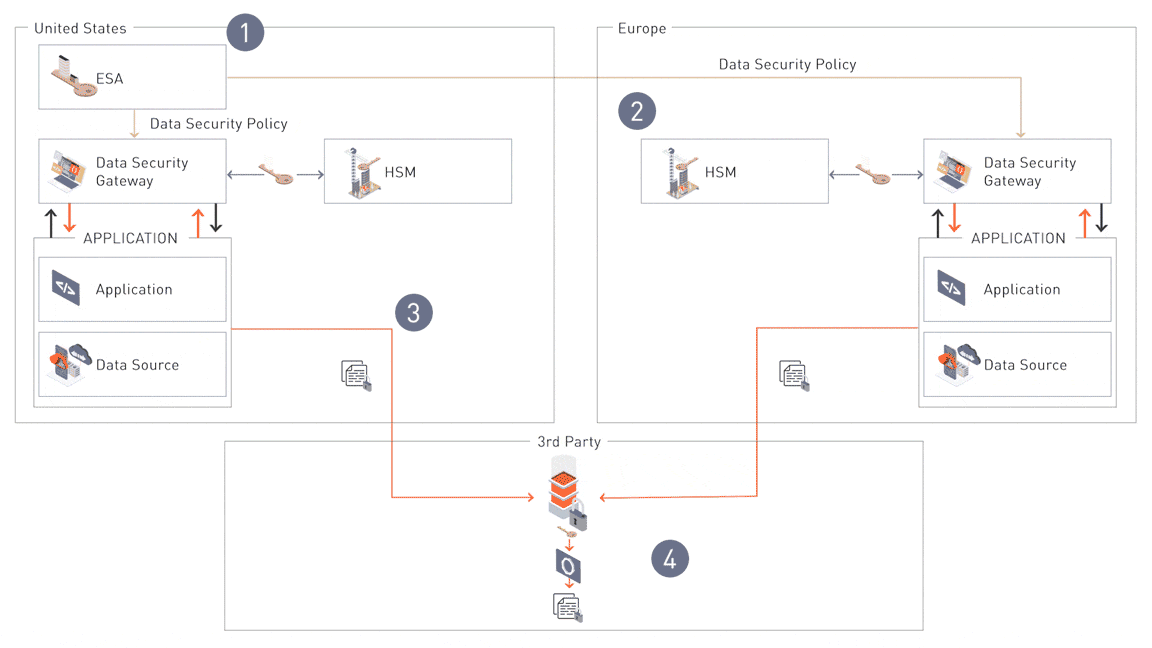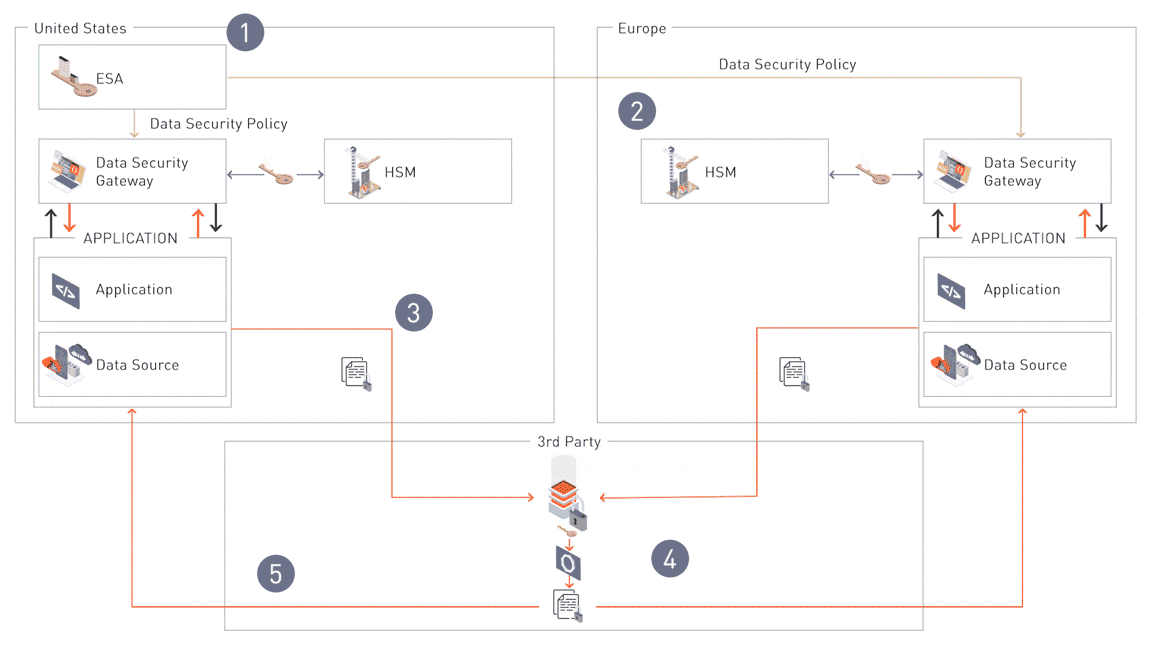
Step 1: Centralized Policy Management
The Enterprise Security Administrator (ESA) serves as the central hub where security teams define and manage data security policies. These policies dictate how data is tokenized, encrypted, and shared, ensuring consistency across all environments. Policies are deployed from the ESA to downstream components like the Data Security Gateways (DSGs).
Step 2: Regional Policy Distribution
Once defined, policies are distributed to the Data Security Gateways (DSGs) and customized for regional compliance. For instance, policies are reshuffled and applied to Hardware Security Modules (HSMs) to create unique codebooks for each region (e.g., Switzerland vs. the EU). This ensures sensitive data is protected based on regional regulatory requirements during sharing.
Step 3: Application-Level Data Protection
Applications interact with protectors (Database Protectors or Application Protectors) via APIs to tokenize or encrypt data at runtime. Depending on the regional policy applied by the DSGs, the same input generates a different tokenized response for each region. This ensures secure and compliant data sharing across regions, protecting sensitive information throughout its lifecycle.
Step 4: Secure Data Sharing with Authorized Third Parties
For collaboration, compliance, or business needs, data is securely shared with authorized third parties while adhering to governance and operational requirements. This step ensures both usability and regulatory compliance.
Step 5: Securing Data with Hardware Security Modules (HSMs)
Hardware Security Modules (HSMs) provide an additional layer of protection, securely managing cryptographic keys before data is shared externally. This ensures that data remains encrypted and safeguarded during every step of the sharing process.
Empower Secure and Compliant Data Sharing
Frequently Asked Questions
01
How does Protegrity ensure data sharing remains compliant with different international regulations?
Protegrity’s platform applies region-specific data protection policies, such as tokenization and encryption, to meet varying regulatory requirements, including the GDPR in Europe and HIPAA in the U.S. Our centralized governance system ensures compliance across borders while allowing data to be shared securely.
02
Can Protegrity integrate with our existing data infrastructure for secure data sharing?
Yes, Protegrity integrates seamlessly with various databases, cloud services, and applications, allowing organizations to secure data without major infrastructure changes. Our APIs and connectors support flexible integration, ensuring data remains protected wherever it’s stored or shared.
03
How does Protegrity help organizations maintain control over shared data?
Protegrity enforces role-based access controls, allowing organizations to restrict data access to authorized personnel only. This granular control ensures that sensitive data is only accessible to the right people, whether internally or with external partners, reducing the risk of unauthorized access.
04
What are the benefits of using Protegrity’s tokenization for data sharing?
Protegrity’s vaultless tokenization replaces sensitive data with tokens, maintaining usability while securing the original data. This approach allows organizations to share data for analytics and operations without exposing sensitive information, ensuring privacy and compliance across multiple regions.
Take the next step
See how Protegrity’s fine grain data protection solutions can enable your data security, compliance, sharing, and analytics.
Get an online or custom live demo.