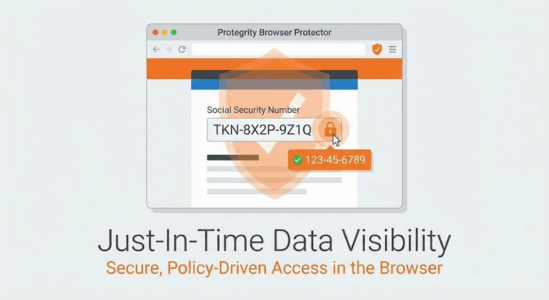
Protect
Your Data
in AI Models
use in AI systems without slowing teams or breaking compliance.
Define Policy Once.
Enforce It Everywhere.
Traditional security was built to control infrastructure and identities.
AI requires security that governs data.
Protegrity decouples policy, enforcement, and cryptography to enable secure computation on protected data — enforcing governance in real time across on-prem, cloud, and SaaS.
Users — Apps — Models
- Compliance
- Quantum
- Sovereign Data
- Secure Agents
- Secure Inferencing
-
Control
Plane- Discovery & Classification
- Centralized, Agentic Policy
- Real-Time Audit & Observability
-
Execution
Plane- API & Endpoints
- Semantic Tokens & Guardrails
- Pseudonymization & Anonymization
-
Advanced
Cryptography- Vault & Vaultless
- Queryable Encryption
- Iceberg Encrypted Data Type
Data — Systems — Code
- Distributed Enforcement
- On-Prem, Cloud, SaaS
- Agent, Proxy, SDK
Secure, Production-Ready AI Pipelines
Most AI projects stall when sensitive data can’t be used safely in production workflows.
Protegrity removes the security, risk, and compliance barriers that slow progress or block AI deployments.
Query enterprise data using natural language without exposing sensitive fields — enabling analytics that remain accurate, explainable, and governed in production.
Orchestrate agents that retrieve data, reason across systems, and take action — while data stays protected and agent behavior remains auditable and production-ready.
Augment models with enterprise data without leaks or compliance violations — with secure, governed access, retrieval, and generation end to end.
Share data across teams and systems without duplication or exposure — with protection that travels with the data, enabling collaboration while maintaining control.
Drive Growth
Reduce Risk
ACHIEVE COMPLIANCE
THE LATEST
FROM PROTEGRITY
Progress That Sticks: Advancing Women in Tech Through Systems and Accountability — Protegrity Perspective
International Women’s Day is a moment to celebrate progress—but also to be honest about what still hasn’t changed. VMblog’s International Women’s Day 2026 roundup brings together perspectives from leaders across…
Shadow Repositories in Chat Apps: How Discord Can Leak Sensitive Context
For many teams, Discord has become the quickest place to collaborate—especially for developer communities and support. The problem is that speed can also turn chat history into a “shadow repository”…
Age Verification at Scale: Avoiding Biometric Retention and Mission Creep
Age verification is quickly shifting from a niche requirement to a default “access layer” for everyday online participation. A recent Cybernews feature uses Discord’s rollout as the jumping-off point to…
See Your
Data Made
Safe for AI
Explore how Protegrity protects sensitive enterprise data across analytics, cloud, and AI.